| Essential | Purpose | Security Header |
| Yes | Enforce HTTPS | Strict-Transport-Security |
| Yes | Prevent Clickjacking | X-Frame-Options |
| Recommended | Prevent XSS | Content-Security-Policy |
| Recommended | Prevent MIME-Sniffing | X-Content-Type |
| Optional | Control Referrer Data | Referrer-Policy |
| Optional | Restrict Browser | Permissions-Policy |
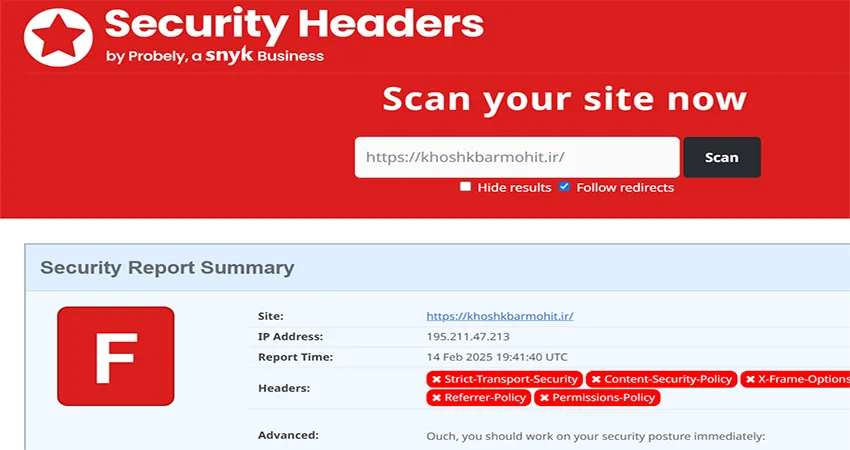
first step: check Security Headers
check your link site in this URL
Security Headers to Enhance Website Security
In today’s digital landscape, website security is a major concern for website owners. Even if your site uses HTTPS, neglecting HTTP security headers can leave it vulnerable to cyber threats. One of the simplest yet most effective ways to boost security is by configuring these headers in your .htaccess file or server settings
Identifying Your Website’s Web Server
Before configuring security headers check, it is essential to determine which web server your site is running on
For WordPress websites, you can check this information through
Site Health → Info → Server section
Submitting a support ticket to your hosting provider
Nginx, Apache, LiteSpeed
Setting Up Security Headers with AI Assistance
it is necessary to access the .htaccess settings, where the entire content should be copied and pasted into the AI chat. Following this, the AI should be requested to analyse the existing configurations and merge the necessary security header codes according to the web server in use
Disruption Due to Security Header Configurations
In the event of website downtime resulting from the utilisation of a plugin or AI-generated code, it is imperative to have previously stored the original `.htaccess` file in a discrete folder. This precautionary measure enables expeditious restoration of the previous code in the event of any emergent issues, thereby ensuring seamless resolution
Probable Causes: The deployment of security plugins, such as Wordfence or AIOS, has the potential to interfere with security header configurations
first creat Backup
Analysis of Security Header Factors
To determine which security header factors are essential for your website, the best reference for scoring and final evaluation is Cloudflare
Configuring Security Headers with Cloudflare
Without a doubt, Cloudflare is the most convenient and reliable tool for automatically configuring security headers check for your website. By simply changing your DNS settings, you can seamlessly implement these security enhancements
In this article, we’ll explore six essential security headers check and explain why you should use them
Security Headers by Plugin
Adding **security headers** to your WordPress site is a critical step to enhance security and prevent attacks like XSS, clickjacking, or code injection. These headers (e.g., `Content-Security-Policy`, `X-Frame-Options`, and `Strict-Transport-Security`) are included in server responses and control browser behavior
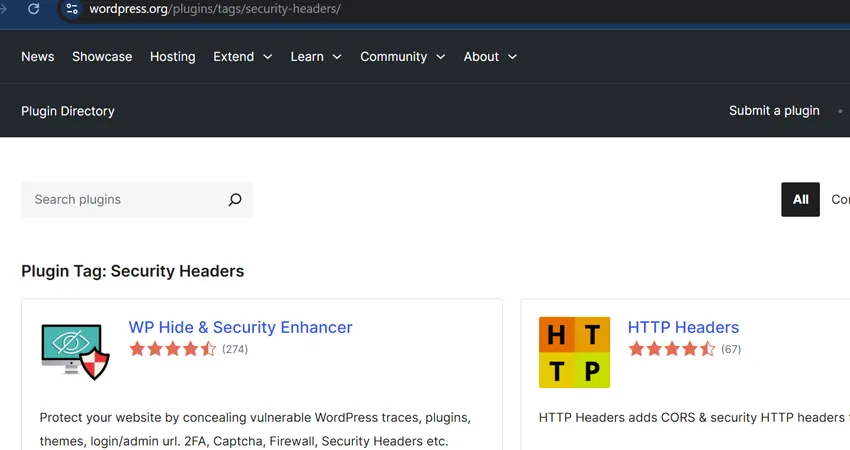
Top WordPress Plugins for Managing Security Headers
From the official WordPress repository, we recommend these plugins for professional security header configuration
https://wordpress.org/plugins/tags/security-headers/
۱. **[WP Security Headers](https://wordpress.org/plugins/wp-security-headers/)**
– **Features**:
– Configure advanced headers like `CSP`, `HSTS`, and `Referrer-Policy`
– Simple interface, no coding required
– Compatible with most themes and plugins
۲. **[iThemes Security](https://wordpress.org/plugins/better-wp-security/)**
– **Features**
– Comprehensive security plugin with header configuration
– Options like `X-Content-Type-Options` and `X-XSS-Protection`.
– Additional tools: malware scanning, brute-force attack prevention
۳. **[HTTP Headers](https://wordpress.org/plugins/http-headers/)**
– **Features**:
– Supports 20+ security headers (e.g., `Permissions-Policy`, `Feature-Policy`)
– One-click activation for essential headers
– Online header testing to verify configurations
Security Headers Check list
Strict-Transport-Security (HSTS) – Enforcing HTTPS
Why is it important?
If your site allows access via HTTP, hackers can use Man-in-the-Middle (MITM) attacks to steal sensitive user data
🔹 Recommended .htaccess configuration
apache
CopyEdit
Header always set Strict-Transport-Security “max-age=31536000; includeSubDomains; preload”
________________________________________
X-Frame-Options – Preventing Clickjacking
✅ Why is it important?
Attackers can embed your website inside a malicious iframe, tricking users into unknowingly submitting their data
🔹 Recommended configuration
apache
CopyEdit
Header always set X-Frame-Options “SAMEORIGIN”
________________________________________
Content-Security-Policy (CSP) – Preventing XSS and Malicious Scripts
✅ Why is it important?
Cross-Site Scripting (XSS) attacks can inject malicious scripts into your site. CSP helps by restricting which scripts can be loaded
🔹 Recommended configuration
apache
CopyEdit
Header always set Content-Security-Policy “default-src ‘self’; script-src ‘self’ https://trustedscripts.com”
________________________________________
X-Content-Type-Options – Preventing MIME-Sniffing
✅ Why is it important?
Some browsers attempt to “guess” the file type, which can lead to executing malicious scripts
🔹 Recommended configuration
apache
CopyEdit
Header always set X-Content-Type-Options “nosniff”
________________________________________
Referrer-Policy – Controlling Referrer Header Data
✅ Why is it important?
When users click on a link, the destination website can receive referrer information from your site. With Referrer-Policy, you control what data is shared
🔹 Recommended configuration
apache
CopyEdit
Header always set Referrer-Policy “no-referrer-when-downgrade”
________________________________________
Permissions-Policy – Restricting Browser Features
✅ Why is it important?
This header limits website access to browser features like camera, microphone, geolocation, and sensors to enhance privacy
🔹 Recommended configuration
apache
CopyEdit
Header always set Permissions-Policy “geolocation=(), microphone=()”
________________________________________
Expect-CT
✅ Why is it important
Ensures TLS certificate transparency to prevent CT-related attacks
Example: Expect-CT: max-age=86400, enforce
________________________________________
Cross-Origin-Opener-Policy (COOP)
✅ Why is it important
Prevents Tab-Napping attacks and protects user sessions
Example: Cross-Origin-Opener-Policy: same-origin
All factors
X-XSS-Protection (non-standard)
Expect-CT
Access-Control-Allow-Origin
Access-Control-Allow-Methods
Access-Control-Allow-Headers
X-Content-Security-Policy
X-Content-Type-Options
X-Frame-Options
X-Permitted-Cross-Domain-Policies
X-Powered-By
Content-Security-Policy
Referrer-Policy
HTTP Strict Transport Security / HSTS
Content-Security-Policy
Content-Security-Policy-Report-Only
Clear-Site-Data
Cross-Origin-Embedder-Policy-Report-Only
Cross-Origin-Opener-Policy-Report-Only
Cross-Origin-Embedder-Policy
Cross-Origin-Opener-Policy
Cross-Origin-Resource-Policy
Permissions-Policy
Strict-dynamic
Strict-Transport-Security
FLoC (Federated Learning of Cohorts)
Golden tips for Elementor speed up



2 پاسخ
Security headers is important
Perfect Article